How to Handle Failed Salesforce AppExchange Security Review? A Guide for Salesforce ISVs
This blog offers practical tips for Salesforce ISVs to overcome repeated AppExchange security review rejections, highlighting the review's importance for app security, credibility, and user trust.
Understanding Salesforce AppExchange Security Review
Listing a solution on the Salesforce AppExchange is a dream for all ISVs. However, this dream comes with a significant hurdle: the notoriously stringent Salesforce AppExchange security review passed by less than 50% of apps submitted on AppExchange.
To ensure the security and integrity of the entire ecosystem, Salesforce meticulously scrutinizes every app submitted to the AppExchange, focusing on these critical areas:
Data Security
User Authentication
Session Management
Network Security
Vulnerability Testing
Common reasons for a ‘FAILED’ Salesforce AppExchange Security Review
The most common reasons for failing a Salesforce AppExchange security review can vary, but they often include issues such as:
1. Mishandling sensitive data, such as storing it in an unencrypted format or transmitting it insecurely over the network.
2. Leaving vulnerabilities such as injection flaws e.g., SOQL injection, cross-site scripting (XSS), or insecure direct object references (IDOR) that attackers could exploit.
3. Failing to implement proper authentication and authorisation mechanisms can lead to unauthorised access to sensitive functionality or data.
4. Misconfigurations in the application or underlying infrastructure can create security weaknesses that attackers can exploit.
5. Failure to keep third-party libraries and dependencies up-to-date can expose the application to known vulnerabilities.
Read More on the official Salesforce Blog > Top 20 Vulnerabilities Found in the Salesforce AppExchange Security Review.
Next steps after AppExchange security review failure
#0 Understand Security Compliance for AppExchange
Getting excited and leaving security aside when prototyping an App idea is usual. 1st security review failure gives a shock to many ISVs, and its time to 1st fix learn the basics:
Bookmark this page - Security Requirements for AppExchange Partners and Solutions. This is an excellent singular index from the official ISVForce guide.
Security Policy Requirements > For Architects & Security experts in your team, responsible for security audits, compliance (HIPAA, etc), documentation, etc.
Prevent Secure Coding Violations > For Developers and Architects to ensure they are not repeating well-documented AppExchange mistakes.
Also covers Secure Your B2C Commerce Solution & Secure Your Tableau Accelerator, if you are building one.
Salesforce Secure Coding Guidelines > These guidelines are general golden rules for all Salesforce solutions, not just AppExchange.
#1 Decoding the Failure Report
The security review report details specific findings concerning vulnerabilities, misconfigurations, or non-compliant practices and categorizes them based on their severity (critical, high, medium, low).
Check the screenshots of a sample security review report below representing various issues raised by Salesforce. Note that Salesforce always provides the following information in its review report:
As highlighted in red , a link is always given to help you learn how to fix the reported issue.
Specific code snippets impacted by that particular issue
Any applicable screenshots, especially in the case of:
Frontend code (LWC, Aura, or Visualforce).
Issues reported by the Automation test failure tools.
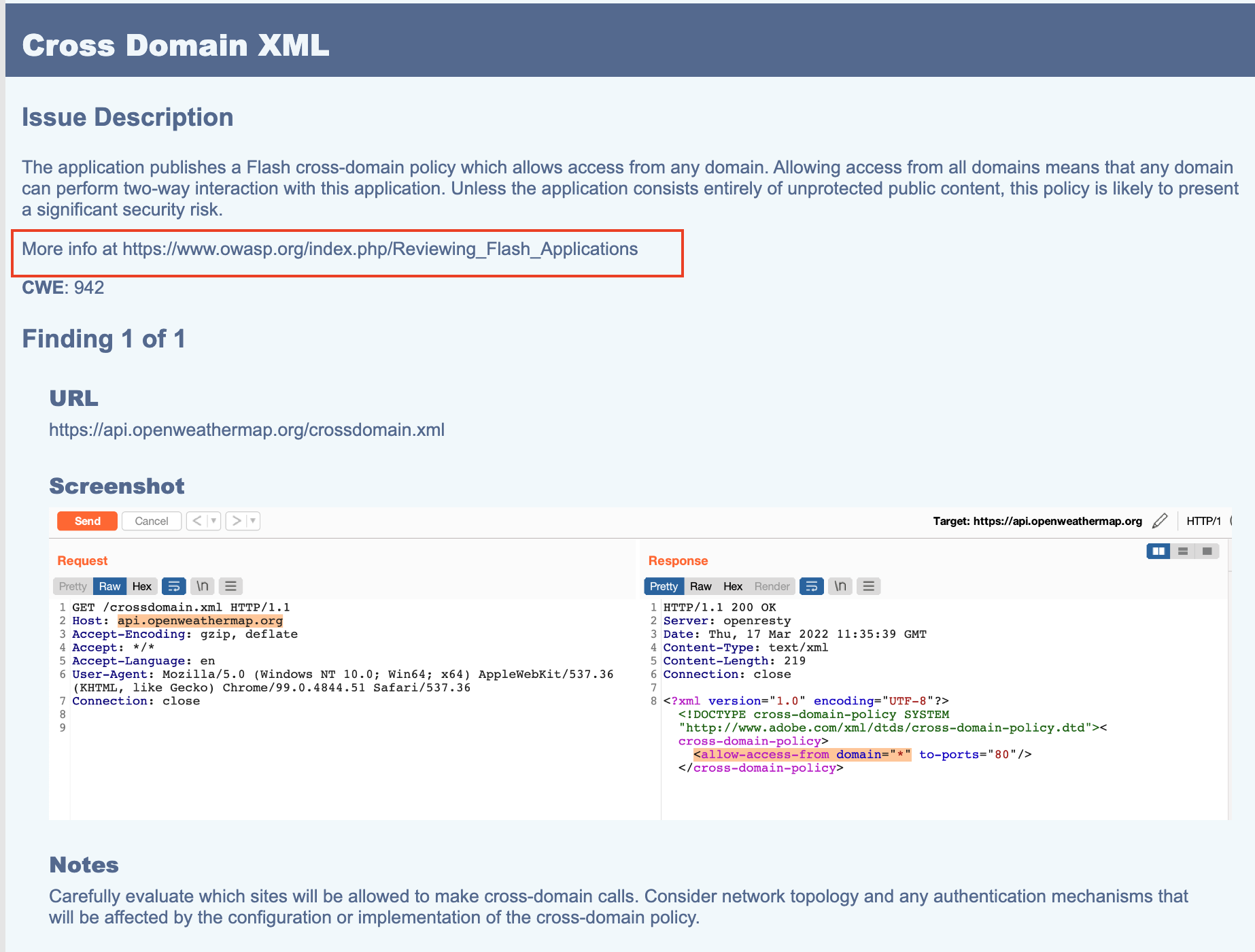
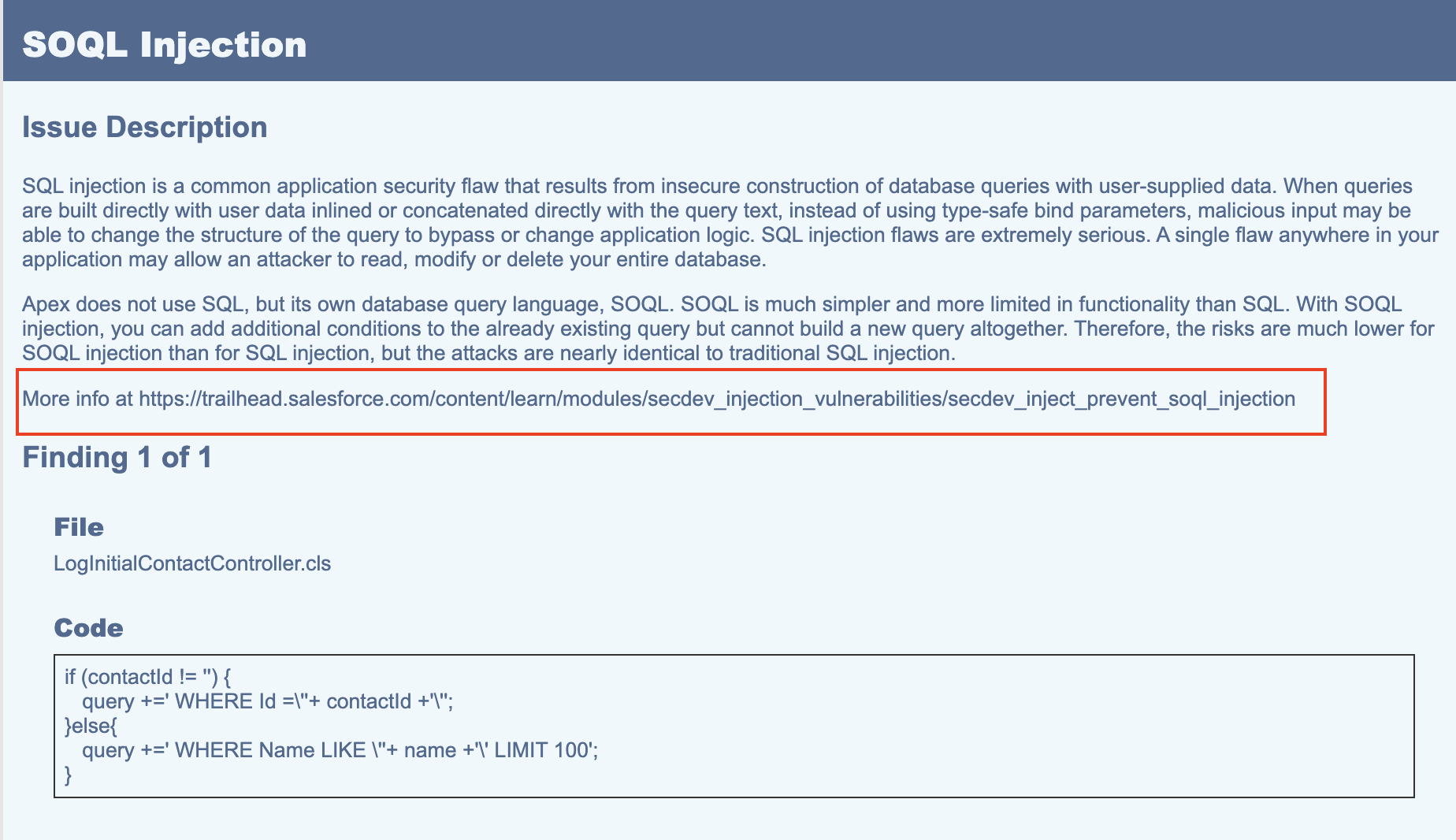

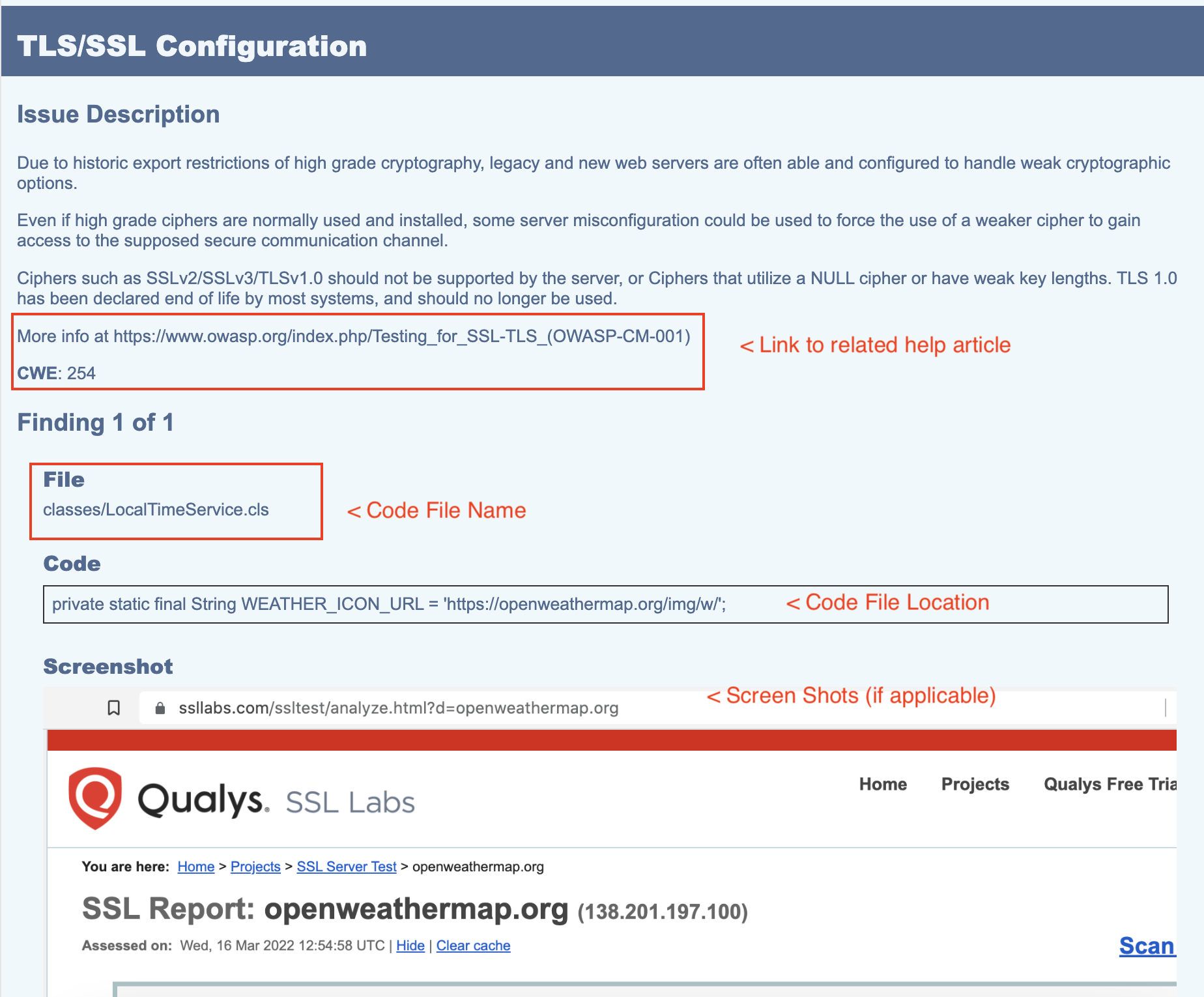
#2 Fixing the Issues
After understanding the issues, take decisive action to patch the weaknesses in the app. This might involve:
Code updates: Patching vulnerable code sections with secure alternatives.
Configuration adjustments: Correcting insecure configurations or settings (such as poor password management practices).
External library updates: Updating the app's outdated or vulnerable third-party libraries(if any). This is mostly the case with JS library inclusions, or any open-source dependencies in Apex, Aura, LWC or Visualforce.
After implementing fixes, thoroughly test the app to ensure the vulnerabilities have been addressed and no new issues have been introduced.
#3 Document false positives
If the Salesforce security team has flagged some issues that don’t seem to be potential security risks, document them as false positives. However, before doing so, thoroughly analyze the flagged issue and how it relates to the app's functionality and code.
Here are some considerations for preparing a FALSE positives report:
Technical documentation: Explain the intended behavior of the code or configuration in question and how it adheres to secure coding practices.
Industry best practices: Provide references to established security recommendations that support your approach.
Alternative explanations: Offer alternative interpretations of the flagged scenario and demonstrate why it doesn't pose a genuine security risk.
Document the Case: Clearly and concisely document reasoning as a false positive. Explain justification in a professional and detailed manner, addressing the specific concerns raised in the report.
Engage with the Security Team: When resubmitting the app, include false positive documentation along with any necessary updates or fixes. Engage with the AppExchange security team if required, providing any additional information or clarification they might need.
Read More:
Possible scenarios after addressing all issues
Once all issues are addressed, it is time to request a follow-up review. These are the possible scenarios after resolving the issues highlighted in the review report:
If the solution is remediated and there are no false positives: In this scenario, begin with a fresh review, provide the required information, and request a follow-up review (fee applies).
If the solution is remediated with false positives: Start a new review, upload a false-positives report, provide the required information, and request a follow-up review (fee applies).
If only documented false positives: If no significant security vulnerabilities are found, consider uploading a false-positives report in the existing review (no fee).
Refer to the official Salesforce Doc — Feedback About Your Completed Review on the next steps after completing the initial review.
For Salesforce AppExchange security review fee-related questions, read the blog Cost Questions Answered: Salesforce AppExchange Security Review Fees FAQs.
Requesting a Follow-up Review After Initial Failure
Encountered an initial AppExchange security review failure but have already addressed the concerns? Here's how to request a successful follow-up review:
#1 Determine the situation
A follow-up review can be requested for one of the following scenarios:
a) New package version: Fixed issues in a managed package and need to review the new version.
b) Managed Package with Revised Code and False Positives: Changed to address security concerns in a managed package and believe some initial findings were false positives.
c) API-only solution: Only addressed code running externally to Salesforce or for an API-only solution?
d) False positives: Believe the initial review identified were false positives.
2. Follow the appropriate steps
a) For New package version: Generate a new package version first. Then link it to the AppExchange Partner Console and submit the updated version for review. Ideally, it takes Salesforce 4 weeks to complete the review after verification.
Read More: Request a Follow-Up Security Review for a New Package Version
b)For Managed Package with Revised Code and False Positives: Addressed the identified vulnerabilities and believe some findings were false positives. Simply resubmit through the AppExchange Partner Console. However, there’s a fee for retesting a remediated solution.
Read More: Request a Follow-Up Security Review for a Managed Package with Revised Code and False Positives
c) API-only solution with false positives
Fixed security issues outside Salesforce or in an API-only solution? Simply, create a new solution (not a new version), connect it to the AppExchange Partner Console, and Submit the new solution for review.
Read More: Request a Follow-Up Review for API-only Solution With FALSE positives
d) API Solution with Revised Code and False Positives
Addressed code vulnerabilities in API solution with FALSE positives? Request a follow-up review by starting a new review from the Solutions page in the AppExchange Partner Console. To submit the remediated solution and false-positives documentation, you’ll be required to pay a fee.
Read More: Request a Follow-Up Security Review for an API Solution with Revised Code and False Positives
By following these steps and addressing the specific situation, one can successfully request a follow-up security review in Salesforce AppExchange.
Strategies for AppExchange success during Resubmission
Successfully navigating the Salesforce AppExchange security review requires a proactive approach to secure the application. Here are some key strategies to gain success in the resubmission:
Technical Adjustments
Self-assessment: Conduct thorough self-assessments before submission, utilizing tools like the Salesforce Code Scanner and following their secure coding guidelines.
Data Security: Implement robust data encryption (at rest and in transit), enforce granular access controls using permission sets and profiles, and avoid storing sensitive data unnecessarily.
User Authentication: Enforce strong authentication protocols like multi-factor authentication and implement secure password management practices.
Session Management: Utilize secure session tokens with short lifespans and employ robust session management mechanisms to prevent unauthorized access.
Network Security: Ensure secure communication channels using HTTPS and avoid transmitting sensitive data in plain text.
Vulnerability Testing: Regularly perform vulnerability testing using both manual and automated tools, addressing identified weaknesses promptly.
Process Improvements
Threat Modeling: Integrate threat modeling into development lifecycle to identify and mitigate potential security risks early on.
Secure Coding Practices: Train developers on secure coding practices and enforce code reviews to identify and address potential vulnerabilities.
Testing: Conduct comprehensive security testing throughout the development lifecycle, including:
a) Manual penetration testing and automated security scans.
b) Scan all external API endpoints, even those not on Salesforce.
c) Test the app for security breaches from different user personas (profiles, permission sets).
d) Keep track of incorrect security alerts and fix any code that doesn't meet Salesforce security rules.
e)Carry out simulated attacks based on the OWASP Top 10 vulnerabilities
f)Conduct rigorous code reviews based on the official Salesforce secure coding violations guidelines.
Documentation: Maintain clear and concise documentation of best security practices and controls, facilitating communication with the Salesforce security team.
Additional Tips:
Stay Informed: Stay updated on the latest security best practices and Salesforce security guidelines to ensure the app adheres to the evolving standards.
Seek Guidance: Utilize available resources from Salesforce, including the AppExchange Security Review documentation, Salesforce ISV Partners, and the Partner Community, for valuable insights and support.
Resources and Tools
Here’s a compilation of all the essential resources, tools, and Salesforce documentation that can aid in the preparation for Salesforce security review.
Security Requirements for AppExchange Partners and Solutions
The Top 20 Vulnerabilities Found in the AppExchange Security Review
Video: How to Submit Your Solution for the AppExchange Security Review
Summary
Recurrent setbacks in security evaluations can be emotionally and financially draining. However, with proper measures and assistance, these challenges can be overcome with ease. Consider double-checking the submitted code, documentation, and review report shared by the security team before resubmitting the solution for security review.
FAQs
-
The duration of the Security Review process for resubmission can vary depending on the complexity of the issues identified and the extent of the changes made to address them. Typically, it may take several weeks to complete the review process for resubmitted apps.
-
Staying up-to-date on the latest changes to the AppExchange security review process is essential for maintaining compliance. You can subscribe to Salesforce's official communication channels, join relevant community forums or groups, and regularly review documentation and resources provided by Salesforce.
-
Use the Security Review Submission Requirements Checklist Builder in the Salesforce Partner Community to generate a checklist tailored to your solution's requirements
Get in Touch
Drop a note with your queries to move forward with the conversation 👇🏻



